Would you let almost anybody into your home? Of course not, you validate the identity of the person before you open the door, either with a simple “who is there”, or you might even have a security camera system in place. All of this, because you know how crucial it is to keep your home and yourself safe from bad actors. While you take so much care with your physical identity and assets, it is crucial to extend this safety to your digital identity as well. Especially if you run a business with several people accessing various applications and digital assets all the time—authentication is not an option, it is a must.
In this read we will discuss the following:
What are different factors of authentication?
What are the different types of authentication?
What is adaptive authentication?
Understanding the difference between authentication, authorization and encryption?
What’s next for authentication?
What is authentication?
Authentication is the process of verifying one’s identity when they access a digital asset. It is the practice of verifying the user is who he/she claims to be. When a user request access to a resource, his/her identity is verified by asking for data such as a password against the credentials that already exist in the database. If the password provided by the user is the same as the one in the database then the user is allowed to access to resource.
This provides the system with the control to ensure only the right users access a resource be it an application, server, document and so on. In today’s time of security breaches, it is crucial to carry out authentication. However, password is only a mere example. Authentication has evolved by leaps and bounds since its inception with simply ‘username’ and ‘password’. It is now about authenticating users by multiple factors, and with various methods to not just verify users but to verify users smartly.
How does authentication work?
The technology of authentication has gone beyond the basic challenge and response password. We will explain it in the coming sections. But, let’s first understand the basic authentication method, how it all started and carried out.
The basic idea of the workings of authentication is simple—you are a user who needs access to an application, for example, Salesforce. To provide you with this access, the application has to verify whether you are who you claim to be. This can be achieved by challenging you with a task/question whose answer, ideally, only you are supposed to know.
(The word ‘ideally’ is key in this read because the real-life situations with passwords is much more complicated than on paper.)
Once you respond appropriately with the correct answer, you will now be allowed to use the application. Your response knowledge is an assured stamp of identity in this case. The application assumes it is indeed you who is requesting access.
This was from an end-user perspective, what happens internally to carry it out?
The basic authentication mechanism is called the HTTP authentication. Here the application verifies the user using the user ID and password that is stored using the HTTP protocol. The HTTP and HTTPS protocols are stateless. This means they do not remember you!
Each time a user wants to access the resource, every request is treated as a new one. The user has to be authenticated over and over again.
To tackle this problem, session/cookie based authenticated was introduced. This requires tokens to be assigned to the user’s session which ensures their authenticity.
Upon the initial authentication a token is stored in the cookie of the end user application and every time a request is made, this token is sent.
The token is removed only upon logout. This method is an advancement from the basic authentication but it also requires a lot of memory to store the token. One user might seem seamless to manage, but consider the case of multiple users. As many users try to access the application the memory required to manage the tokens causes the overhead of the server to increase as well. This among other drawbacks led to the rise of several other authentication practices that are in use today. This is why authentication today is done using several methods, consider different factors and not just a password.
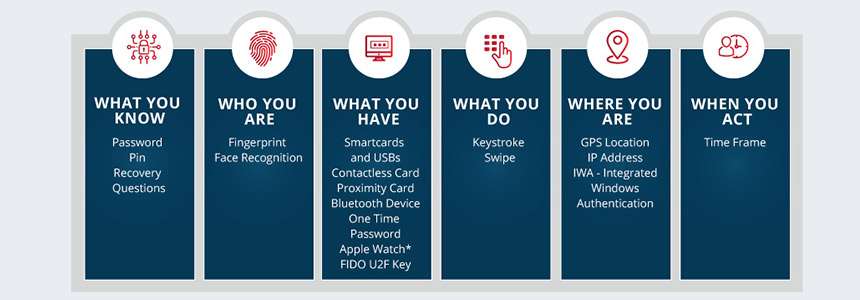
What are different factors of authentication?
Factors of authentication refers to the different methods through which a user is authenticated. These factors are unique to each individual. There are 5 factors of authentication with which they request can be validated.
The 5 factors of authentication:
Something you know
This is also known as the knowledge factor. Something you know entails the information that you know to obtain access to a resource and verify your identity. This is the premise of challenge response questions as well. These questions can be set by you to ensure it is you who is accessing it.
Remember how we spoke about ideally something that only you are supposed to know? The reality of something you know might differ from the ideal situation. Suppose the challenge response question is, “What is the name of your pet?”. Keep your dog in mind, you might’ve excitedly set this up. But, with the same excitement, you might’ve also posted a couple of cute pictures of your dog. Now, if hackers want access to this question, one glance at your social media and the deed is done. You have enabled a hacker to hack you.
Something you have
A report stated how 51% of respondents in a study claimed to use the same password across the business as well as personal accounts. This is a huge cause for worry. That’s why, only password authentication isn’t enough. Hence, there are many other factors to verify identities besides passwords. ‘Something you have’ refers to something that you possess ‘physically’. This could be your phone. Your phone belongs to you and if you enabled security locks such as a pattern or PIN then only you could access it. This is done via methods like One Time Password (OTP). If someone tries to make a payment with your card information, then they would need an OTP to confirm the payment. Since the OTP comes to you, owing to your number being connected with the account, you could notify the bank of suspicious activity and block access. Smart cards that are used to swipe access are also something that can be used to authenticate something you have.
Something you are
This factor refers to the attribute that you are. Your physical characteristics such as fingerprint, retina, voice, face can all be used to verify your identity. This is a highly secure method as these attributes cannot be taken advantage of easily as they uniquely belong to you at all times.
Somewhere you are
This factor refers to your location. The commons methods to determine this are using Internet Protocol (IP) addresses or Media Access Control (MAC) addresses. Suppose you log in everyday from India and within the next hour, there is a log in request from Chicago. This is physically impossible and will enable you with a notification of a suspicious login.
Something you do
This factor describes your identity as an entity. Your behaviour, the way you interact with your phone, laptop, applications are all indicators of your identity. These are driven by behavioural analysis using Machine Learning that learns your characteristics daily. The feature of windows 8 called Picture Password is an example of this factor. It enables authentication based on how you interact with a picture.
What are the different types of authentication?
Two-factor authentication:-
This authentication method is as the name suggests—requires two factors to authenticate you. Logging in to create a new account in application is a classic example. Initially, the application asks you to enter your phone number. The mobile phone to which you have serves as one way to authenticate along with a follow up OTP generated on your phone—a code which only you possess.
Multi-factor authentication:-
This authentication requires you to verify your identity in multiple ways. Say you want to login to an application, after the initial login process with a username and password which is something you know, the application might prompt you to verify your identity using fingerprint authentication which is something you are. These different types of authentication methods help alleviate the authentication process.
Soft tokens and hard tokens:-
These methods of authentication rely on something you have. Soft tokens are similar to OTP generated authentication, which is a unique code sent to you with a limited amount of time to utilise it. Hard tokens are something that you can physically carry to authenticate such as a smart card, USB drive, etc.
Out of band authentication:-
This method of authentication is an extension of two-factor authentication requiring using two different channels to verify a user’s identity. This is used for highly secure data such as for financial transactions. If you have requested payment on your computer, then another verification for the same might be needed on your phone over a call.
Biometric authentication:
Biometric authentication is the verification using the factor of something you are. Finger print, iris, facial recognition among other fall under this category.
Passwordless authentication:-
This type of authentication include every authentication method that does not verify you through passwords but other means such as biometrics or OTP.
What is adaptive authentication?
Adaptive authentication is the next step in carrying out authentication techniques. This method also known as risk-based authentication, adapts to the user’s behaviour and mechanics. Then once there is a deviation in this behaviour such as time of login, it introduces step up authentication—another factor to verify identity. Thus, whenever a user logs in, a risk score is generated based on the user’s deviation from the usual behaviour and sensitivity of the document in question.
A brochure of the company product has lesser sensitivity as compared to a document consisting of a company’s financial information. Whenever a user tries to access the latter, the risk score automatically increases. Either step up authentication is used or the access is blocked altogether.
Understanding the difference between authentication, authorization and encryption?
Authentication, Authorization and Encryption are often terms used interchangeable owing to their similar mechanics. But, all three of them play different roles.
Authentication, as discussed in this read, is a method of verifying the identity of the user. This is done using passwords, 2FA, MFA, biometrics, OTP and so on.
Authorization, is the method of ensuring the identity is entitled to receive access to the resource requested. In an organization, when a user requests access to an application, his/her entitlements are checked to see if they are eligible to this access. If not, the access is not provided even if they have been authenticated.
Authentication is essentially the first step followed by authorization.
Related read: The difference between Authentication and Authorization
Encryption, is the method of masking a sensitive information. When someone logins in using their username and password, then their password must be encrypted and stored. This means the password is not visible to anyone. The encrypted password can be decrypted only once someone has the key to do so. Some encryption algorithms are Data Encryption Standard (DES), Advanced Encryption Standard (AES) and so on.
What’s next for authentication?
Authentication has evolved over the last few years owing to the security risks that exist today. Simple user name and password do not cut it anymore. Authentication methods such as biometric, OTP are replacing passwords. In advanced techniques risk based authentication methods are leading.
With changing threat landscape, changing the way identity of users are authenticated is a necessity. Although passwords aren’t completely going away, they can be combined with other methods to level up your security.
Grow with the changing times, secure yourself, and not just with a password!